-
Flashback: Declassified 1970 DOD cybersecurity document still relevant | Ars Technica
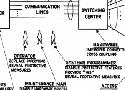
June 26, 2016 03:17:56 PM GMT+02:00 * - permalink - - http://arstechnica.com/security/2016/04/flashback-declassified-1970-dod-cybersecurity-document-still-relevant/The Ware Report's outline of what it takes to create a secure system also remains relevant:
The system should be flexible; that is, there should be convenient mechanisms and procedures for maintaining it …The system should be responsive to changing operational conditions, particularly in time of emergency. The system should be auditable…The system should be reliable from a security point of view. It ought to be fail-safe in the sense that if the system cannot fulfill its security controls, cannot make the proper decisions to grant access, or cannot pass its internal self-checks, it will withhold information from those users about which it is uncertain, but ideally will continue to provide service to verified users. The system should be manageable from the point of view of security control. The records, audit controls, visual displays, manual inputs, etc., used to monitor the system should be supplemented by the capability to make appropriate modifications in the operational status of the system in the event of catastrophic system failure, degradation of performance, change in workload, or conditions of crisis, etc. The system should be adaptable so that security controls can be adjusted to reflect changes in the classification and sensitivity of the files, operations, and the needs of the local installation. The system must be dependable; it must not deny service to users…'The system must automatically assure configuration integrity. It must self-test, violate its own safeguards deliberately, attempt illegal operations, monitor communication continuity, monitor user action, etc., on a short time basis.